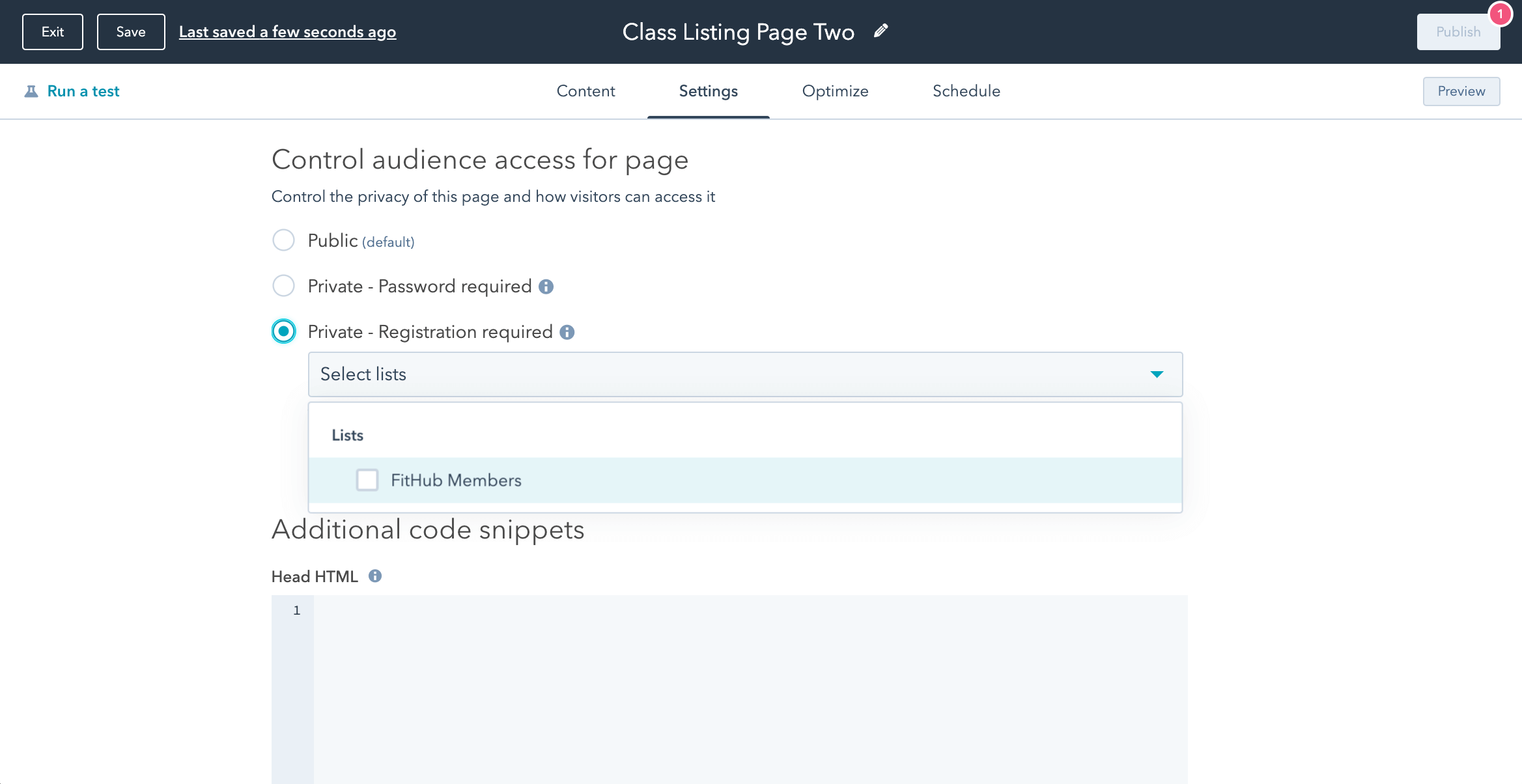
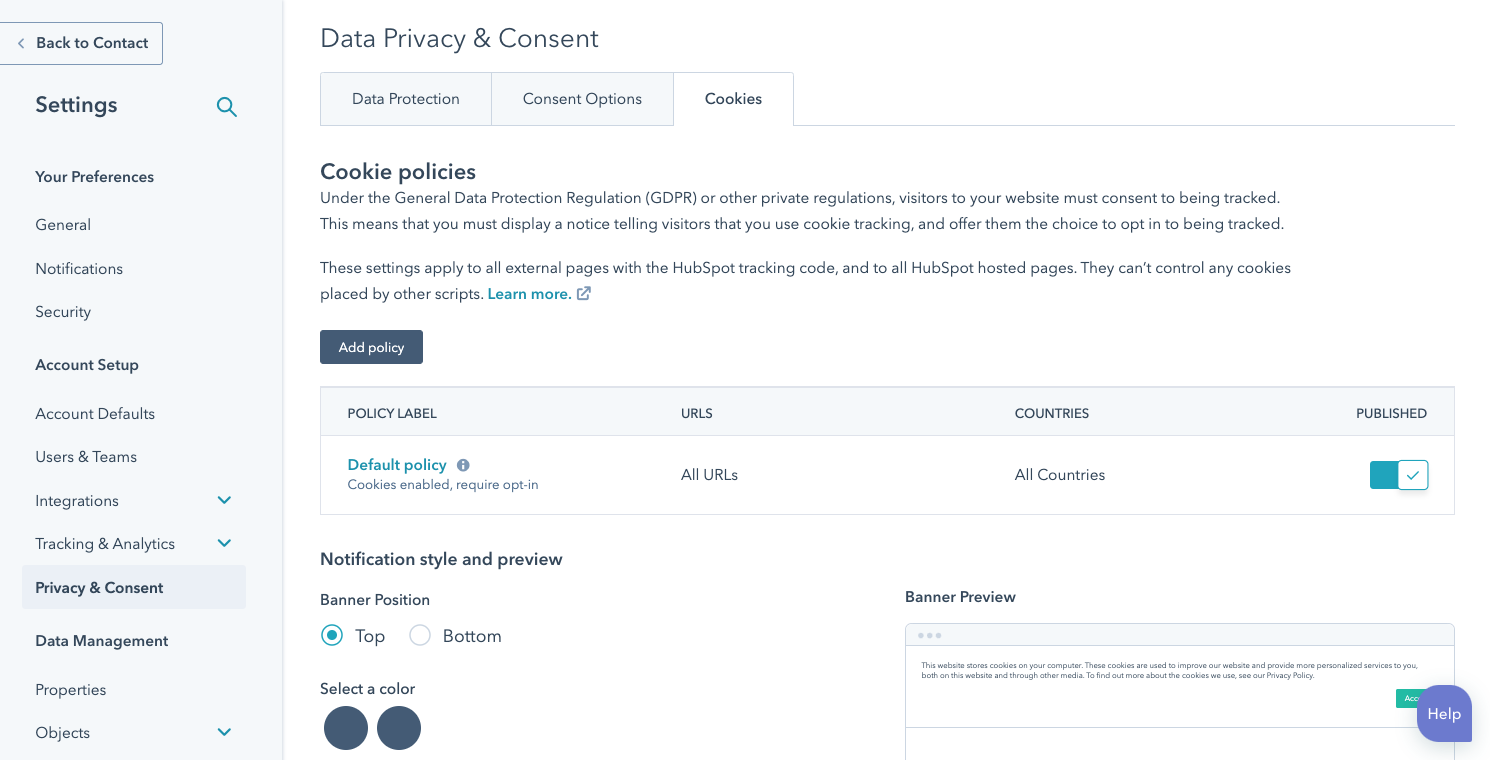
Crafted, not cobbled
When your tools are cobbled together without a solid foundation, each tool has a different standard for security or protocols for controlling data. Too much data spread across systems leaves gaps and cracks.
HubSpot is crafted, not cobbled.
Our product team takes a forward-thinking approach to privacy and security with the “Mainsail”, a framework for building a secure, reliable, and consumer-grade product. We don’t build anything new unless we are meeting the security and privacy standards we’ve laid out.